If you’ve tried creating a provider hosted app for SharePoint 2013 onprem (not in Office 365) you know you likely need to go through some gyrations to set it up for high trust using the server-to-server (S2S) protocol. There’s a great article on MSDN that walks you through the details of this (linked below), but it’s a pain to have to type all that. Hopefully Visual Studio 2012’s SharePoint 2013 & Office 2013 Developer Tools will make our lives easier when we get to RTM, but for now in Beta 2 / Preview, I find it to be a pain.
Introducing the first installment to Critical Path Training’s SharePoint 2013 Script Library. This is located in the Critical Path Training Members section of our site, specifically in the Code Samples section. A sign in is required, but it’s free to set one up. The script PrepareS2SApp.ps1 does almost everything for you.
PrepareS2SApp.ps1 Usage
This assumes you’ve already set up your developer environment for creating apps. If not, check this MSDN article: HOWTO Set up an On-Premises Development Environment for Apps for SharePoint.
You’d ideally run this script before building your provider app. You first need a certificate… you can follow the instructions on the MSDN article linked below, specifically just the section Create a Public & Private Test Certificate. Then pick a name for your app… this must be unique to your site. Next, run the script. It will do everything in the MSDN article linked at the bottom of this post, except for the public & private certs, for you. It accepts the following arguments:
Required Parameters:
- $AppDisplayName: Display name of the application. This must be unique.
- $TargetSiteUrl: URL of the site collection where the app will be installed.
- $CertPath: Fully qualified path to the *.cer certificate created prior to running this script.
Optional Parameters:
- $AppGuid: Unique GUID for the app. This must be all lowercase. If not provided, one is automatically generated & displayed at the end of the script.
- $AllowOAuthOverHttp: Configures the STS to allow HTTP OAuth. Default = TRUE
- $SupressTrustedSecurityTokenIssuerDisplay: Suppress displaying the output of the New-SPTrustedSecurityTokenIssuer cmdlet.Default = TRUE
- $SupressAppPrincipalDisplay: Suppress displaying the output of the Register-SPAppPrincipal cmdlet.Default = TRUE
If you run the script, here’s what you should see:
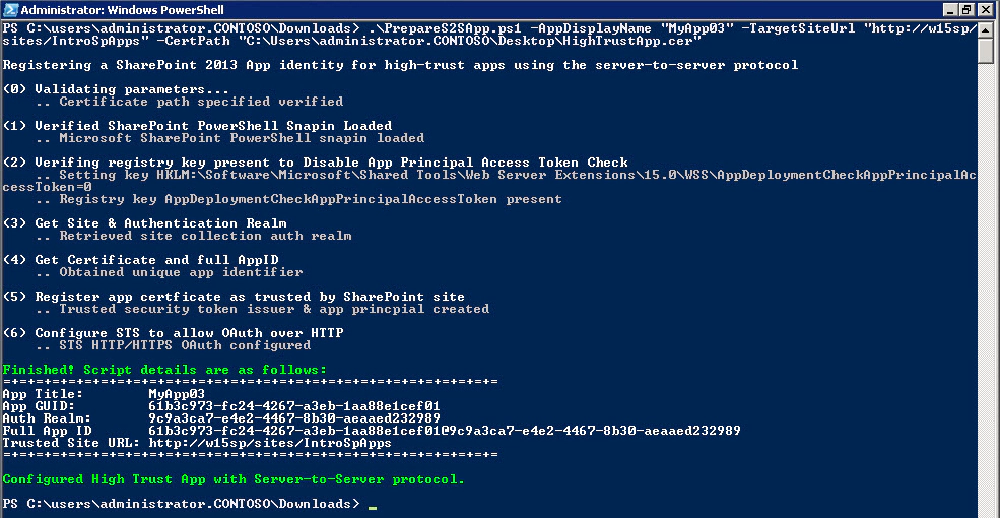
Running the script
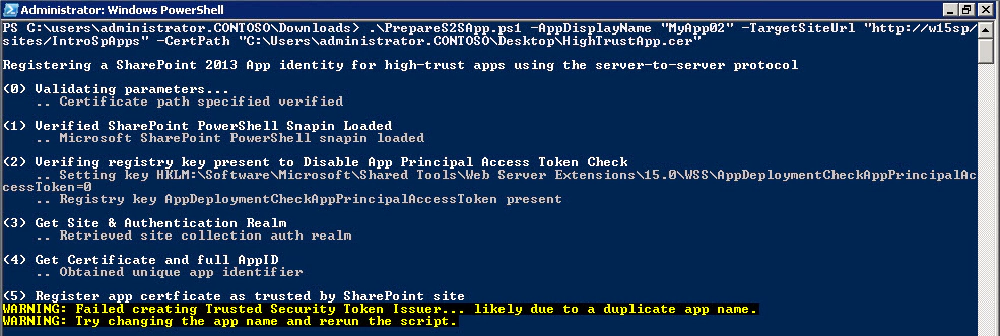
If you don’t provide a unique name for your app, you’ll get a warning message and the script will stop proceeding: